Penetration testing and red teaming are popular security testing methods that organizations can use to identify potential vulnerabilities in their IT infrastructure. While both methods share some similarities, they differ in their goals, scope, and methodology. In this article, we will explore the differences between Pen Testing vs Red Teaming, and provide scenarios when either should be utilized by an organization.
Penetration Testing
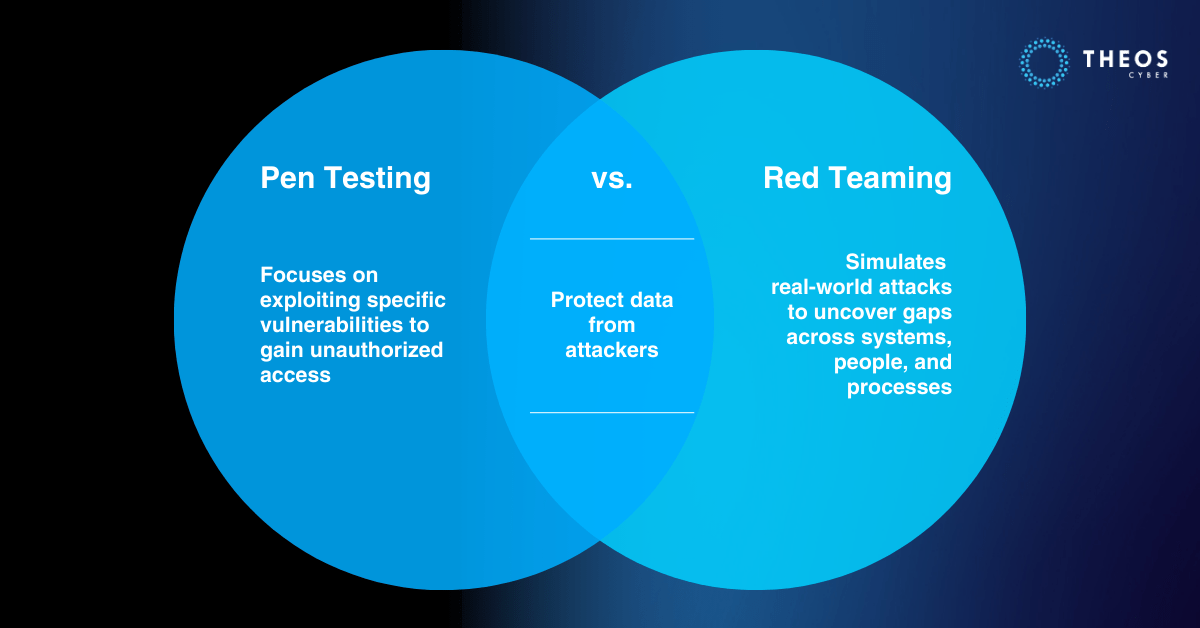
Penetration testing, also known as pen testing, is a method of testing an organization’s IT infrastructure to identify potential vulnerabilities and exploit them to gain unauthorized access. The goal of pen testing is to simulate an attack and identify weaknesses in an organization’s security defenses. This is done by using various tools and techniques to attempt to penetrate the organization’s network, applications, and systems.
Pen testing can be conducted in different ways, such as white-box, black-box, or gray-box testing. In white-box testing, the testers have full access to the system’s source code and other information, while in black-box testing, they have no prior knowledge of the system. Gray-box testing falls somewhere in between, with the testers having partial access to the system’s information.
Pen testing can be useful for organizations in various scenarios, such as:
- Many compliance standards, such as PCI DSS, HIPAA, and SOC 2, require regular penetration testing to ensure the security of sensitive data.
- Pen testing can help organizations identify potential security risks and vulnerabilities that may have been missed by other security measures.
- When an organization makes significant changes to its IT infrastructure, such as implementing new systems or applications, pen testing can help ensure that these changes do not introduce new vulnerabilities.
- Regular pen testing can help organizations stay on top of their security posture and ensure that their security measures are effective in protecting against potential attacks.
Red Teaming
Red teaming is a more comprehensive approach to security testing that simulates a real-world attack on an organization’s IT infrastructure. Unlike pen testing, which focuses on exploiting vulnerabilities, red teaming aims to identify potential weaknesses in an organization’s overall security posture. Red teaming involves a team of security experts, also known as red teamers, who use various tactics, techniques, and procedures (TTPs) to gain access to an organization’s systems and data.
Red teaming is often conducted using a customized approach, where the red teamers tailor their methods and TTPs to the specific organization and its security defenses. The goal of red teaming is to identify potential vulnerabilities that may have been missed by other security measures and to provide recommendations for improving an organization’s overall security posture.
Red Teaming can be useful for organizations in various scenarios, such as:
- Red teaming is particularly useful for organizations that operate in high-security environments, such as government agencies, military organizations, or financial institutions, where the consequences of a security breach can be severe.
- Red teaming can be useful when an organization is considering a merger or acquisition, as it can help identify potential security risks and vulnerabilities in the target organization’s IT infrastructure.
- Red teaming can be used as a training tool for employees, IT staff, or security personnel, to help them understand the tactics and techniques used by cybercriminals and how to defend against them.
- Red teaming may be required by some compliance standards, such as NIST 800-53 or ISO 27001, to ensure that an organization’s security measures are effective in protecting against potential attacks.
Choosing Between Pen Testing and Red Teaming
When deciding between pen testing and red teaming, organizations should consider their specific needs, goals, and budget. Pen testing is often a more straightforward and cost-effective.
In conclusion, both pen testing and red teaming are valuable security testing methods that organizations can use to identify potential vulnerabilities in their IT infrastructure. While pen testing focuses on exploiting specific vulnerabilities, red teaming takes a more comprehensive approach to identify weaknesses in an organization’s overall security posture. Organizations should choose the appropriate testing method based on their specific needs, goals, and budget. Regular testing, whether through pen testing or red teaming, is essential to staying on top of an organization’s security posture and ensuring that security measures are effective in protecting against potential attacks.
About THEOS Cyber
THEOS Cyber is a cybersecurity services firm headquartered in the Asia-Pacific region, specializing in helping organizations protect digital assets and manage cyber risk. We provide elite digital forensics and incident response (DFIR), managed threat detection and response (MTDR), and offensive security services including red teaming and penetration testing. Our teams work closely with regulated industries—financial services, fintech, healthcare, critical infrastructure—to deliver rapid, expert support across the full cyber incident lifecycle. THEOS Cyber strengthens resilience through technical depth, operational readiness, and legal-aware guidance.

